What is Gitlab?
DevSecOps: Integrating product security at every stage of the SDLC

The software development lifecycle (SDLC) has taken on different forms since its evolution. The field has witnessed the application of various philosophies, each bringing its own set of improvements.
Today, DevOps is the driving force behind most software development projects. However, since Security is not integrated into DevOps, security teams must work separately from the development team. In short, Security is out of the scope of development and operations and is handled manually, destabilizing the automated DevOps cycle.
The core principle of DevSecOps is the integration of Security into the entire software development lifecycle, from the very beginning of the development process through deployment and maintenance. This means that Security considerations and practices are not treated as a separate function or afterthought but are integrated into every aspect of the software development process. Let’s dive into the details to learn more about the features of DevSecOps and how to implement the DevSecOps lifecycle.
What does DevSecOps offer?
Firstly, DevSecOps clarifies that “security is everyone’s responsibility” while maintaining development speed.
Thus, DevSecOps can exist without the use of additional security-checking software. DevSecOps helps to reduce delays between code delivery from the Dev platform to Security and back, saving time and resources. This is achieved by incorporating Security into the software development, testing, and deployment.
Usually, Security SDLC is an innovation and rapid development obstacle. With DevSecOps, the test code is subjected to all security checks, and project teams do not have security issues such as random attacks, hacks, and downtime.
In the security integration process, DevSecOps provides several key benefits to its users, namely:
- Use a set of testing procedures, including integration, unit, etc., to prevent regression and improve the quality of each release, thereby saving a significant amount of time.
- Identifies vulnerabilities at every stage, which reduces project risks.
- Works according to the principle of project security, which involves providing developers with automated testing mechanisms.
- Uses an appropriate branching and tagging approach for source control management (SCM) and automatically generates release notes to provide all stakeholders with a complete understanding.
- Ensures that every build is successful and that a consistent and effective problem-solving mechanism is in place in the event of a failure, encouraging collaboration across teams.
- Empowers team members to analyze KPIs and improve the DevSecOps process.
- Uses Blue-green deployment to respond quickly to changes.
- Allows teams to seamlessly use the same processes and tools for applications, regardless of the programming language they are written in.
- It helps to avoid reputational damage by preventing the possibility of a breach through enhanced auditing and monitoring.
What is the difference between DevOps and DevSecOps?
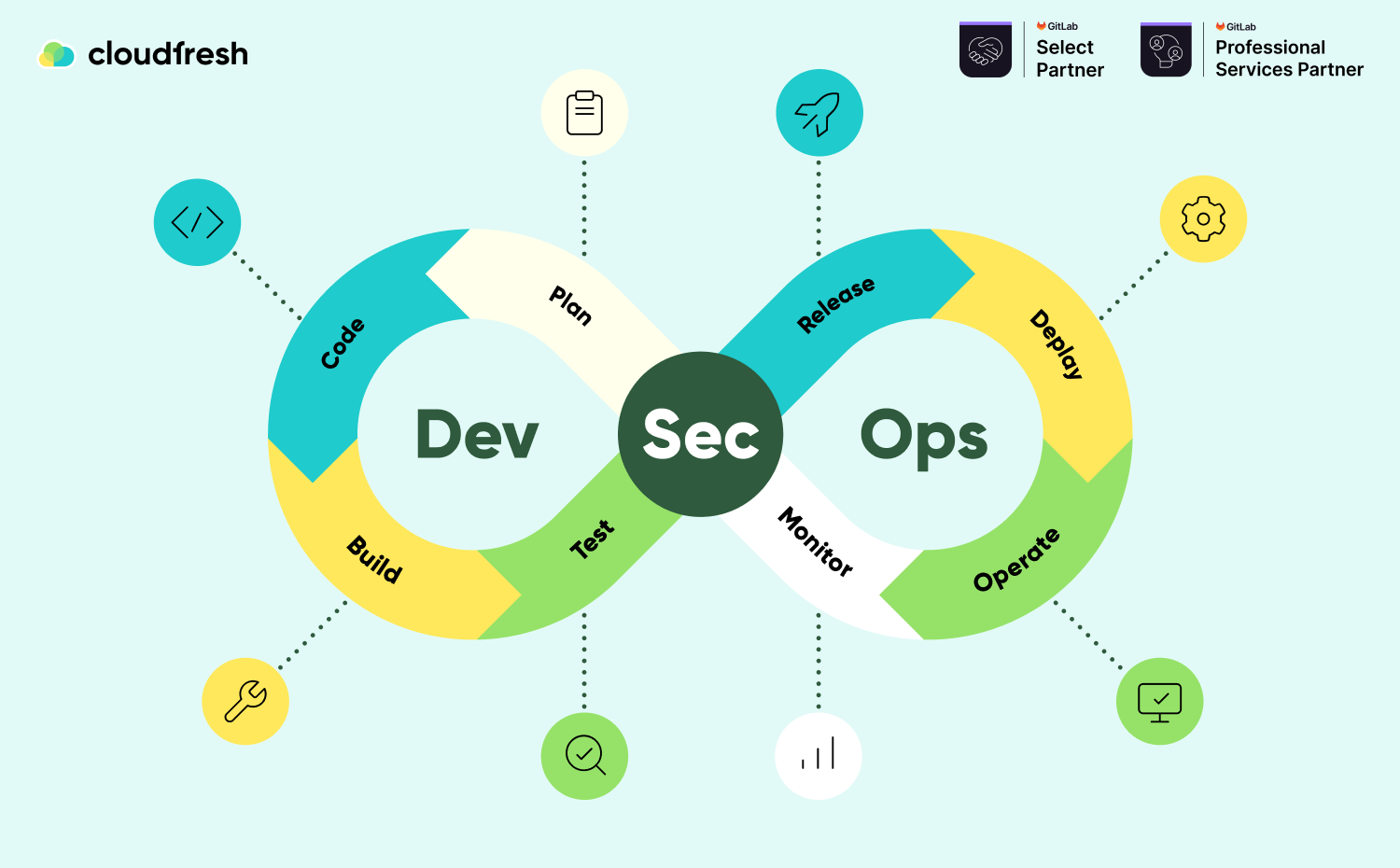
How SDLC stages change when implementing DevSecOps
Planning
The planning phase of DevSecOps is the least automated and is only possible with collaboration, discussion, review, and a security analysis strategy. Teams must conduct a security analysis and develop a testing schedule that specifies where, when, and how testing will be shown.
IriusRisk, a collaborative threat modeling tool, is a popular DevSecOps planning tool. Collaboration and communication tools like Slack and issue management and tracking solutions like Jira or Asana also exist.
Code
Developers can create more secure code with DevSecOps technologies at this stage by using code review, static code analysis, and pre-commit intercepts, which are essential security procedures.
Each commit and merge automatically triggers a security checkout or validation when security technologies are directly integrated into the existing Git workflow of developers. These technologies support a variety of integrated development environments and many programming languages. Some popular security tools include PMD, Gerrit, SpotBugs, CheckStyle, Phabricator, and Find Security Bugs.
Build
The “build” stage begins when the source repository code is developed. The main task of DevSecOps build tools is to automate the security analysis of the output build artifact. Static application software testing (SAST), unit testing, and software component analysis are the essential security procedures. Tools can be implemented into the existing CI/CD pipeline to automate these tests.
Third-party code dependencies, which can come from an unknown or untrusted source, are often installed and built by developers. In addition, dependencies on external code can inadvertently or maliciously introduce vulnerabilities and exploits. Therefore, reviewing and checking these dependencies for potential security flaws during development is crucial in the DevSecOps phases.
The most popular tools for creating a build phase analysis include Checkmarx, SourceClear, Retire.js, SonarQube, OWASP Dependency-Check, and Snyk.
Test
The test phase begins when the build artifact is successfully created and delivered to the staging or testing environments. Running a complete set of tests requires a significant amount of time. Therefore, this phase should happen quickly to save more important tests for the final step.
Dynamic Application Security Testing (DAST) tools are used throughout the testing process to detect application flows such as authorization, user authentication, API-connected endpoints, and SQL injection.
Numerous paid and open-source testing tools are available on the current market. Supported features and language ecosystems include BDD Automated Security Tests, Boofuzz, JBroFuzz, OWASP ZAP, SecApp suite, GAUNTLET, IBM AppScan, and Arachi.
Release
The application code must be thoroughly tested before the DevSecOps cycle is released. This stage focuses on securing the runtime architecture by reviewing the environment configuration values, including user access control, network firewall access, and personal data management.
One of the main challenges of the release phase is the principle of least privilege (PoLP). PoLP means that each program, process, and user needs minimal access to perform its task. This combines the verification of access tokens and API keys to limit the owner’s entry. Without this auditing, a hacker could stumble upon a key that grants access to unassigned parts of the system.
At the release stage, configuration management solutions are a key security component. At this stage, the system configuration can be reviewed and audited. As a result, commits to the configuration management repository can be used to change the design, which becomes immutable. Some popular configuration management tools include HashiCorp Terraform, Docker, Ansible, Chef, and Puppet.
Deploy
It’s time to deploy the build artifact to the production stage if the previous process went well. Security issues affecting the current working system should be addressed during deployment. For example, it is essential to carefully check any configuration variations between the current working environment and the original staging and development parameters. In addition, production TLS and DRM certificates should be checked and validated in preparation for future upgrades.
The deployment phase is a good time for verification tools such as Osquery, Falco, and Tripwire. They can collect data from the active system to assess its functioning. Organizations can also apply the principles of chaos engineering by testing the system to increase their confidence in its resilience to turbulence. It is possible to replicate real-world events such as hard disk failures, loss of network connectivity, and server failures.
Operation
Another critical stage is the continued operation of the product, and operations staff often perform periodic maintenance. Operations teams must frequently monitor for zero-day vulnerabilities. DevSecOps can use IAC tools to quickly and efficiently protect the organization’s infrastructure while preventing human error from penetrating.
Monitor
A breach can be avoided if Security is constantly monitored for abnormalities. Therefore, it is crucial to implement a reliable continuous monitoring tool that works in real-time to track system performance and detect any exploits at an early stage.
DevSecOps Best Practices
Implementing the DevSecOps philosophy requires a combination of several approaches and a shift away from the traditional mindset. Below are tips to improve the process here and now:
- Measure the time lost in dealing with vulnerabilities after code merging. Next, find a pattern in the type or source of these security vulnerabilities and make adjustments to improve.
- Identify the software pain points and risks between development and Security, create a plan to address them, and then execute that plan.
- Make small changes to the code. More minor updates are easier to review and defend and can be rolled out faster than monolithic project changes.
- Automate and integrate security scans. Perform scans everywhere to check every change to secure code and identify security flaws at the source.
- Build security scanning into the developer’s workflow. Integrated Security allows developers to find and fix vulnerabilities before releasing the code. It also reduces the number of open-source vulnerabilities sent to the security team, making it easier to review them.
- Give developers access to SAST and DAST reports. While this is important for patching, it is also a valuable tool to help developers develop secure coding practices.
- Reduce or eliminate any cascading security processes in your SDLC. You should always be able to change direction if necessary: keep your organization and security controls in place.
- Provide the security team with a view of both resolved and unresolved vulnerabilities in the code, where the vulnerabilities are located, who created them, and their status for remediation.
- Optimize your toolkit so that employees can focus on one interface: a single source of truth.
What about cases?
GitLab helps companies to ensure security protocols that ensure the integrity of the application and compliance with the company’s security policy. I’ll give you a couple of examples below.
One of the cases is the story of Hilti, which has successfully implemented GitLab to provide its own SCM, CI/CD, and security scanning code. With GitLab, deployment time was reduced from three hours to 15 minutes. The development and test teams now own the code and can see potential vulnerabilities in advance. Thanks to GitLab, they could develop software in-house faster than if they had used a complex set of tools.
Another success story is Dunelm, a home furnishings retailer that chose GitLab SaaS Ultimate to integrate tools and seamlessly deploy secure pipelines on the AWS cloud platform.
As Dunelm’s engineering teams transitioned to a targeted serverless architecture, they identified significant gaps in existing CI/CD tools. More automation, better management, Security, and flexibility were needed to integrate various plugins and quickly build robust software pipelines.
Dunelm’s management team chose GitLab CI/CD to enable technical teams to take on performance, testing, and security challenges early and throughout the SDLC. Today, couples can run more complex scans within GitLab pipelines. With SAST/DAST scans, security vulnerabilities are detected much earlier in development, and teams can fix them immediately.
Another good example is how GitLab optimized the work of Zebra, an online insurance comparison platform. In particular, Zebra was using GitHub and Jenkins for deployment, and the large number of plugins led to management difficulties and security issues. After analyzing different platforms, the management chose GitLab, which offers an advanced repository and CI/CD capabilities. In addition, the teams moved from using three tools to using only GitLab CI/CD, which allowed them to automate the process fully. GitLab also ensured Security and compliance with SOC2 certification requirements.
These stories demonstrate how DevSecOps can help organizations significantly improve Security, defect reduction, deployment, and cycle time. You can read more about GitLab case studies here.
A 10-point checklist for security testing
Finally, consider a ten-step DevSecOps security checklist that GitLab uses, which can help your team get in sync and ensure they’re on the right track.
- Understand what is most challenging in your DevSecOps pipeline.
Analyze where Security creates problems in the development process. It may need to be corrected prioritization of fixing code vulnerabilities or the people responsible for this process. Once you understand the bugs in your approach, you can start fixing them.
- Define a common goal.
Because there are so many assumptions about Security and ownership, offering your team clear goals will create a culture where reducing security risks is everyone’s responsibility.
- Conduct an audit to determine where teams are wasting time.
By understanding how much time your team spends on bug fixes after a code merge, you can identify patterns and make adjustments to improve.
- Discuss pain points and vulnerabilities.
By discussing the issues with the entire team, you can create a plan to address each. This discussion helps to ensure that everyone’s voice is heard and to identify pain points that may not be obvious from cold, complex data.
- Make small, incremental changes to the code.
At GitLab, iteration is one of the core values, so when they make changes, they are small, quick to implement, and then evolve. The same principle applies to the transition from DevOps to DevSecOps. Small, incremental code changes are easier to test and secure and can be rolled out faster than monolithic changes to a project.
- Automate and integrate.
Automation and integration are key to DevOps, but they also make Security scanning a powerful tool. If scanning is performed everywhere, every code change will be checked, and vulnerabilities will be found much earlier.
- Make Security reporting transparent.
Instead of keeping the results of static application security testing (SAST) and dynamic application security testing (DAST) in isolation within security teams, make sure this information is available to the entire team, especially developers.
- Determine if you have security processes based on the Waterfall principle.
In the traditional waterfall approach to Security, vulnerabilities are usually discovered at the end of the development cycle. Take the time to audit your existing security workflows as part of your SDLC. If you find any waterfall-style processes, consider eliminating or significantly reducing your reliance on them. You should always have the ability to change direction.
- Ensure the security team has access to information about the status of vulnerabilities.
Security teams need better visibility into resolved and unresolved vulnerabilities, where they are, who created them, and their status for remediation.
- Combine your tools into a single DevSecOps platform.
It’s easier to be responsible for Security when teams need the right tools. The best way to Shift Left Security is with an end-to-end platform that helps DevOps teams move away from Waterfall processes, streamlines communication, enables automation and continuous integration, and provides a single source of accurate data on security scan results and critical vulnerability status.
Conclusion
To summarize, DevSecOps implementation has the following benefits:
- It helps build customer trust by providing specific products and services.
- It prevents the exploitation of system vulnerabilities and improves the system’s overall Security.
- The DevSecOps methodology allows teams to achieve results quickly while ensuring the highest level of Security.
- By integrating Security into the software development process from design to deployment, teams can instantly identify and eliminate potential risks, thereby reducing the risk of malicious attacks.
- DevSecOps helps organizations avoid potential threats and remain competitive in their markets.
Implementing DevSecOps is essential for any team looking to protect themselves from malicious attacks while delivering development quickly and efficiently. In addition, integrating Security into the SDLC ensures that all new applications are secure from the start.
Gitlab and Cloudfresh
Cloudfresh is a certified Consulting, Support, and Implementation GitLab Partner. We empower organizations to get the most from GitLab solutions. With our help, hundreds of teams improve their SDLCs. Check out our professional GitLab services.

Get your GitLab licensing offer. Our GitLab Experts will advise, manage, and implement GitLab high-quality technical solutions.
Use this link for a 30-day free trial for the GitLab self-managed licenses, professional onboarding, consultations, expertise, and technical support from Cloudfresh.
Let’s accelerate your DevSecOps transformation together!