DORA Metrics: Helping Firms Find Dev Productivity Insight
GitLab Strengthens Security, Broadens Duo as Part of Q1 2025 Updates
🤖 GitLab Duo and AI Features
The new Duo Code Review (beta) contributes to development efforts by running initial reviews on merge requests. It flags potential bugs and suggests improvements—just tag @GitLabDuo as a reviewer or mention it in a comment to kick things off.
Duo Self-Hosted reached general availability, opening the door to running selected large language models (LLMs) on top of your own infrastructure. You can plug in open-source Mistral models (via vLLM or AWS Bedrock), Claude 3.5 Sonnet (on AWS Bedrock), or OpenAI models (on Azure OpenAI), all tailored for Code Suggestions and Chat. Integration with VS Code and JetBrains IDEs has also leveled up. Dragging project files into Duo Chat gives it a richer understanding of your codebase, which means more accurate explanations, smarter debugging, and better suggestions.
Root Cause Analysis for GitLab Duo Self-Hosted has entered beta for self-managed instances. It supports models from Mistral, Anthropic, and OpenAI GPT, helping you troubleshoot failed CI/CD jobs faster by digging through logs, surfacing the issue, and recommending fixes. The full rollout is on track for 17.11.
The Duo Chat interface is now resizable within the GitLab UI. That means easier multitasking, whether you’re scanning code output or chatting in the background. Juggling multiple conversations? No problem, either. Duo Chat now keeps track of different topics individually. Each thread maintains its own context, and switching between them is a breeze using the chat history icon (the feature is currently exclusive to GitLab.com on the web).
Want to see how AI is impacting your workflow? The AI Impact Dashboard brings fresh insights, tracking month-over-month trends for Code Suggestions acceptance rates and Chat activity. It complements the existing 30-day snapshot and is also available for Duo Self-Hosted users—perfect for spotting patterns and measuring real value.
Looking to experiment with the latest models? Meta Llama 3 is now in beta for GitLab Duo Self-Hosted, supporting both Code Suggestions and Chat. There’s also more flexibility under the hood: each Duo Chat sub-feature in the self-hosted setup can now run on a different supported model, giving you fine-grained control over performance and behavior.
Finally, composite identity adds a security boost by allowing requests to be authenticated as both a user and a service account at once. It’s especially useful for AI agents that need to balance user intent with their own access permissions.
🔎 Code Review and Commit Management
Branch rules became more flexible—configurable squash settings are now part of the mix. You can fine-tune squashing behavior per protected branch. Want to require squashing when merging into develop, but skip it for main? No problem. Tailor it to fit your team’s workflow.
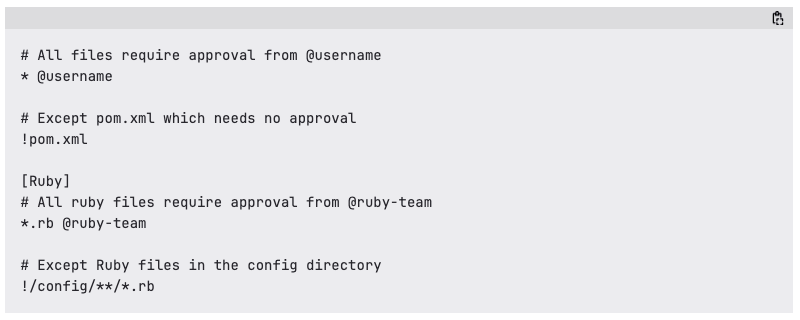
Managing Code Owner approvals is also getting smarter. The CODEOWNERS file now supports path exclusions, so you can specify certain files or directories that don’t need Code Owner sign-off. Cleaner reviews, less overhead.
Even better, you can now assign entire roles as Code Owners—like @@developers, @@maintainers, or @@owners—instead of listing individual users. This makes managing ownership easier and keeps it in sync with project roles rather than specific people.
For those digging through Git history, the blame view has a new trick. You can now toggle visibility for specific revisions flagged in a .git-blame-ignore-revs file. That means cleaner context when reviewing file history—especially useful when ignoring large refactors or formatting-only changes.
🔄 Continuous Integration/Continuous Delivery (CI/CD)
GitLab Dedicated customers now have more disaster recovery options with a richer selection of AWS regions for hosting failover instances. These extra regions give teams more flexibility when planning for resilience.
To tighten compliance and control over pipeline execution, jobs in the .pipeline-policy-pre reserved stage must now be completed before any further stage can begin, regardless of relationships among needs.
Pipeline execution policies have changed as well, now supporting additional merge request variables. Greater pipeline control also comes with the ability to enforce custom stages in Inject mode via execution policies. This adds flexibility to your CI/CD structure while replacing the older inject_ci strategy with the more powerful inject_policy.
- You can now enforce centralized workflow rules for the
override_cistrategy. skip_cibehavior is now configurable in policies, allowing trusted users or service accounts to bypass pipelines—without skipping compliance checks.
For security workflows, you can now manage concurrency in scheduled scan pipelines by defining a time window in your policy to prevent overlapping scans and achieve more predictable execution.
Automatic pipeline expiration is now a configurable project setting. Set a timeframe, and GitLab will remove the outdated pipelines and their artifacts, keeping things tidy and non-manual. On top of that, admins using the community-edition GitLab licenses can now set CI/CD resource limits to better manage usage across projects—keeping pipelines efficient and infrastructure in check.
In the GitOps world, GitLab now supports OCI-based GitOps with FluxCD. This lets you package Kubernetes manifests as OCI images and store them in any compatible container registry, a major step forward in modern GitOps workflows.
GitLab Runners have rolled out with a fresh batch of features and fixes:
- 17.9 added health checks for runner autoscaler instances, histogram metrics for the prepare stage, and support for custom service container names when using the Kubernetes executor.
- 17.10 introduced autoscaler executor health checks, support for expanded Docker executor volumes, and new device configuration options for services.
🛡️ Security and Compliance
Protected repositories now offer tight access controls and granular permissions so only approved users can push, pull, or manage your container images.
Vulnerability management has become more adaptive:
- You can now manually adjust the severity of individual vulnerabilities to better reflect your organization’s risk model. Every change is fully tracked.
- Secret detection now includes remediation guidance, helping teams act faster and more effectively.
- Vulnerabilities can now trigger webhook events, making it easier to automate responses or integrate with third-party tools.
- The system can now identify the commit that resolved a vulnerability, improving traceability and audit readiness.
- Additional risk signals—EPSS, KEV, and CVSS data—are now shown in the Vulnerability Report and Details views to help prioritize the most critical issues.
- You can also filter by identifier in the project-level Vulnerability Report for quick, targeted searches.
On the compliance side:
- You can now select a default compliance framework from the dropdown on the Frameworks page, facilitating setup across top-level groups.
- The UI tab in the Compliance Center has been optimized to handle large numbers of frameworks without performance hits.
- Custom roles can now be granted permission to read the compliance dashboard, allowing for more tailored access control.
- It’s now possible to apply a framework directly from a project’s compliance center, making implementation faster and easier.
Merge request approval workflows are now more powerful:
- You can define multiple, distinct approval actions, giving you more flexibility for complex review processes.
- Custom roles are now supported in approval policies so you can tailor workflows without rigid role constraints.
In policy enforcement, you can now block the deletion of active security policy projects that are linked to groups or projects, preventing accidental or malicious disruptions. And finally, OAuth application authorizations now generate audit events, giving you better oversight of third-party app access.
⌚ Authentication and Authorization
- You can now configure the duration of ID tokens using the
id_token_expirationattribute when GitLab is used as an OpenID Connect (OIDC) provider, allowing for more fine-tuned control over authentication timeframes. - GitLab administrators now have a unified API to identify and revoke tokens.
- Webhook triggers for expiring tokens have been extended. Now, in addition to the previous 7-day warning, events fire at 60 and 30 days before expiry, giving more advanced notice for token renewal.
- Profile attribute mapping has been enhanced, allowing you to map the Organization and Title from an OmniAuth identity provider (IdP) to a user’s GitLab profile.
- The new
self_rotatescope allows you to rotate access tokens (personal, project, or group) automatically, improving token security without manual intervention. - The Credentials Inventory now lets you sort personal, SSH, and project and group access tokens by the owner, creation date, and last use date, helping admins manage and audit tokens more efficiently.
- You can now set a custom expiration date for rotated service account tokens using the
expires_atattribute, offering more flexibility for token lifecycle management. - Multiple OIDC providers are now supported for group memberships, giving you greater flexibility for authentication across different identity providers.
- IP address tracking has been expanded to show up to the last seven IP addresses from which access tokens were used.
- Admins can now disable 2FA for individual enterprise users via the API.
- Inactive project and group access tokens are now visible in the UI for up to 30 days for auditing, so no token is overlooked during security reviews.
- The Group Sharing Visibility feature now provides distinct tabs for Shared projects and Shared groups on the overview page, helping users quickly navigate shared resources.
- Administrators can now restrict users from making their profile private via a special setting in the Admin Area.
- Lastly, project creation permissions have been clarified and improved, making it easier for admins to define who can create projects within groups. The Owner role is now included in the Project creation protection settings.
8️⃣ Kubernetes Integration
Managing your Kubernetes deployments through GitLab has become much more convenient. GitLab-managed Kubernetes resources now handle provisioning and management automatically, making it easier to deploy applications without the heavy lifting.
Navigating your Kubernetes dashboard is also more intuitive. A fresh search bar lets you quickly find specific pods, cutting down on time spent digging through long lists.
And when using Flux, it’s easier to stay on top of what’s happening: reconciliations that are on hold are now clearly marked with a Paused status, giving you better visibility into deployment flow right from the dashboard.
Workspace container support with Sysbox is now available, too. If your development environment runs on a Kubernetes cluster configured with Sysbox, you can build and run containers right inside your workspace—no extra steps needed.
Speaking of workspaces, starting one is now even simpler. There’s no need to define a custom devfile.yaml—GitLab supplies a default file preloaded with common dev tools, so you can get coding faster.
Lastly, a heads-up for users managing certificate-based Kubernetes clusters: GitLab has introduced a new API endpoint that helps you discover and migrate those clusters. This is especially important as support for certificate-based integration will be disabled on GitLab.com and eventually removed from self-managed instances.
📄 GitLab Pages
Accessing private GitLab Pages just got easier for automation and integrations—you can now authenticate programmatically using access tokens. Perfect for scripts, bots, and other tools that need secure access without manual login steps. Group-level access controls are now in place, giving group owners the ability to restrict GitLab Pages visibility to project members only.
Need to host different versions of your site? With parallel deployments, you can now run multiple versions of your GitLab Pages sites at the same time—each one gets a unique URL, so testing and previewing changes is a breeze. And if you’re managing multiple custom domains, GitLab Pages now lets you set a primary one. All traffic will automatically redirect to it—keeping your URLs clean, consistent, and SEO-ready.
🧑💻 Work Items Management
Issues, epics, and tasks now speak the same language—literally. They’ve been unified under a common framework, and the new beta look brings a sleek interface. Think: drawer views for quicker access, the ability to switch item types, support for start dates, ancestry insights, a single development items list, and an improved layout with enhanced linking between related work.
To keep things consistent and efficient, description templates are now available across all work item types—epics, issues, tasks, objectives, and key results.
Managing to-dos just got easier:
- Snooze items to temporarily hide them when the timing isn’t right.
- Use bulk actions to mark items as done or snooze several at once.
- Track multiple to-do items per issue or merge request and receive separate notifications for each mention or action—so nothing slips through the cracks.
In epics, things are more organized than ever:
- A redesigned Epic ancestors widget now sits right at the top, clearly showing both immediate and ultimate parents.
- You can now add parent epics directly, just like with issues.
- The iteration field is now displayed on child items within epics, issues, and objectives, giving you more visibility for planning.
- Epic health statuses (On track, Needs attention, At risk) help communicate progress at a glance.
- You can also track time spent on epics, bringing time management to a higher level.
- And with new webhooks, your external tools can sync with real-time epic updates.
There’s also great news for customization fans: you now have expanded color options for epics, including custom RGB and hex values alongside predefined choices—add some personality (or meaning) to your planning views. In the meantime, developers and data scientists will appreciate that the Work Items GraphQL API has been beefed up with filters for dates, health, and weight, giving you more control over what you query.
Plus:
- Switching between work item types is now fully supported.
- Adding new child items is faster, with the form staying open after each submission so you can keep rolling.
- Notifications for service accounts can now be customized with a specific email address for better communication and clarity.
- Wiki pages now support comments, turning documentation into a collaborative space for discussion and feedback.
📦 Package Registry
GitLab also continues to improve how you manage dependencies and secure your packages:
- GitLab Dependency Proxy now supports authentication with Docker Hub, allowing you to bypass rate limits and access private images with ease. You can configure this directly through the GraphQL API.
- Dependency Scanning has expanded its coverage with support for the pub (Dart) package manager.
- Dependency Scanning also gets a boost for SBOM (Software Bill of Materials) in projects using Cargo, Conda, Cocoapods, and Swift.
- Package registry operations now include audit events to track when packages are published or deleted, providing more visibility into your package lifecycle.
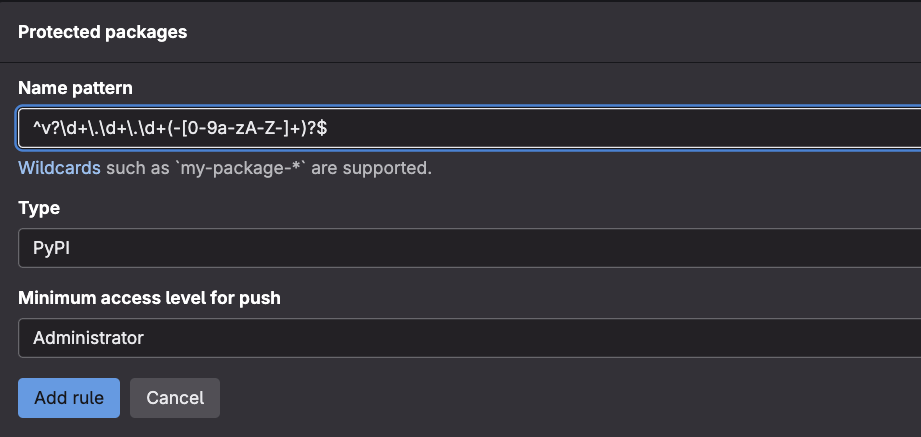
- Protected PyPI packages, adding an extra layer of stability to the package registry. With this new feature, you can safeguard your critical dependencies from unintended changes.
- License scanning support for Swift packages has been added, enabling better compliance tracking for teams using Swift in their projects.
- On the Dependencies list within a project, you can now filter by package name using the Component filter, making it easier to find and manage specific dependencies.
✅ Other Improvements
With the introduction of the beta GitLab Query Language (GLQL) views, users can now create dynamic, real-time work tracking directly within their existing workflows by embedding live data queries in Markdown code blocks. The GitLab Flavored Markdown has also received significant improvements. In particular, the revamped editor experience and content organization make it easier for users to create well-structured documentation that includes complex formulas and high-quality images.
For those looking to track DevOps performance, GitLab has introduced a new visualization of DORA metrics across projects in the Value Streams Dashboard. The Projects by DORA metric panel provides insights into key performance indicators, helping teams assess and optimize their workflows with data-driven insights. Speaking of assessments, machine learning model experiment tracking is now generally available.
Project integrations got way easier with the ability to manage them from a group using the REST API, and workspace extensions now support proposed APIs, which enables developers to create even more customized environments. GitLab also expanded its runner offerings: hosted runners on Linux for GitLab Dedicated are now in limited availability, and large M2 Pro hosted runners on macOS are available in beta.
Who We Are
Cloudfresh is a GitLab Professional Services and Select Partner trusted by teams worldwide. We help you get GitLab working for you—fast. From setup and strategy to hands-on training and straight answers, we make sure you actually get the value you’re looking for across every facet of the platform—Duo (Enterprise) AI included.
Need clarity? We explain the why, not just the how. Got questions? We’re all ears. Want your team to feel confident using GitLab? We’ll get them there. Just fill out the short form below to get started.













